APIwiz
APIwiz
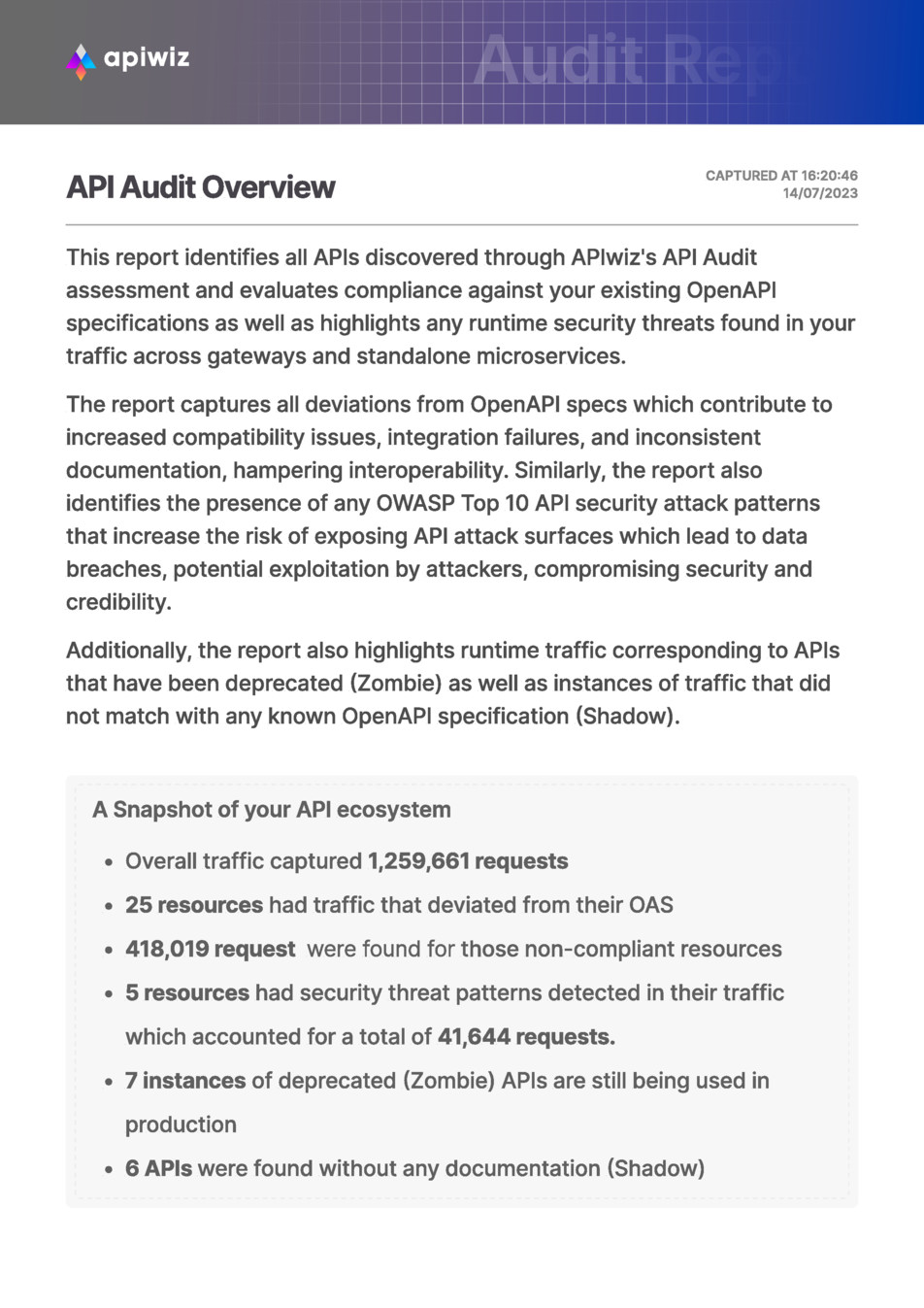
APIwiz API Audit Overview
Summary
The API Audit Overview report by APIwiz highlights the importance of evaluating compliance against OpenAPI specifications and identifying any runtime security threats in traffic across gateways and microservices. The report captures deviations from OpenAPI specs that can cause compatibility issues and integration failures, as well as highlights OWASP Top 10 API security attack patterns that increase the risk of data breaches and exploitation by attackers. Additionally, the report identifies deprecated APIs still in use and instances of traffic not matching any known OpenAPI specification.
(Source: Page 1)
Design Compliance
After analyzing over 1.2 million API requests, it was found that a significant number deviated from OpenAPI specifications, leading to compatibility issues. The breakdown of non-compliant requests showed deviations in request body, response body, query, path, header, and form parameters. Addressing these design compliance issues is crucial for ensuring seamless interoperability and consistent documentation.
(Source: Page 2)
Security Compliance
The analysis of API traffic against OWASP Top 10 security patterns revealed a substantial number of vulnerable requests, including SQL, XPATH, Javascript, and server-side threats. These security vulnerabilities can expose APIs to attacks such as SQL injection, XPath attacks, injection of malicious JavaScript code, and unauthorized access to server-side functions. Mitigating these security risks is essential to protect sensitive data and prevent unauthorized access.
(Source: Page 2)
Deprecated and Ambiguous Traffic
The API audit identified deprecated APIs (Zombie) and ambiguous APIs (Shadow) in the runtime traffic. Deprecated APIs that are no longer actively maintained but still accessible pose security risks, while ambiguous APIs without clear ownership can lead to vulnerabilities. It is crucial to address these deprecated and ambiguous APIs to avoid potential security threats and maintain a secure API ecosystem.
(Source: Page 3)