CAPTURED AT 16:20:46 14/07/2023 This report identifies all APIs discovered through APIwiz's API Audit assessment and evaluates compliance against your existing OpenAPI specifications as well as highlights any runtime security threats found in your traffic across gateways and standalone microservices. The report captures all deviations from OpenAPI specs which contribute to increased compatibility issues, integration failures, and inconsistent documentation, hampering interoperability. Similarly, the report also identifies the presence of any OWASP Top 10 API security attack patterns that increase the risk of exposing API attack surfaces which lead to data breaches, potential exploitation by attackers, compromising security and credibility. Additionally, the report also highlights runtime traffic corresponding to APIs that have been deprecated (Zombie) as well as instances of traffic that did not match with any known OpenAPI specification (Shadow). A Snapshot of your API ecosystem Ó Overall traffic captured 1,259,661 request® Ó 25 resources had traffic that deviated from their OA´ Ó 418,019 request were found for those non-compliant resourceº Ó 5 resources had security threat patterns detected in their traffic which accounted for a total of 41,644 requestsª Ó 7 instances of deprecated (Zombie) APIs are still being used in productioä Ó 6 APIs were found without any documentation (Shadow)
Design Compliance 01 Security Compliance 02 Deprecated and Ambiguous Traffic 04 Zombie API Traffic Details 05 Shadow API Traffic Details 06 Resource Breakdown 07 Remediate with APIwiz 15
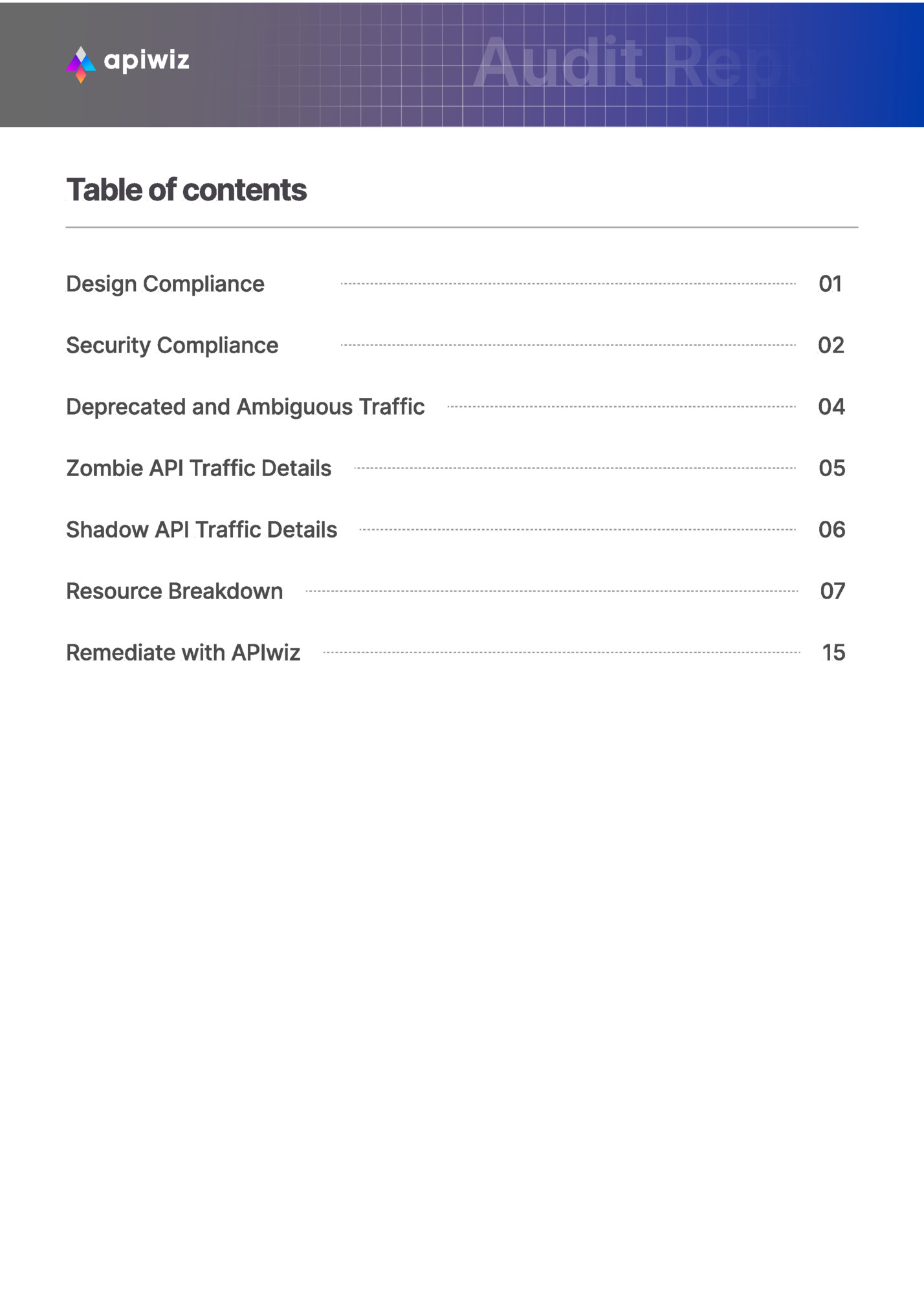
CAPTURED AT 16:20:46 14/07/2023 After analyzing the overall traffic of 1.2 Million API Requests and matching them against known OAS , the below was concluded: op 844,522 requests deviated from their OA lp 418,019 requests were OAS Compliant Compliant 418,019 requests Total requests 1,259,661 844,522 requests Non-Compliant Non-compliant Traffic Breakup Following is the breakdown of all the non-compliant requests based on request body, response body, path, header, query and form parameters. Request Body Response Body Query Path Header Form 524,742 request 211,648 request 108,433 request 0 request 0 request 0 request op 62.15% were request body non compliant and deviated from their OA lp 25.04% were response body non compliant and deviated from their OA rp 12.80% were query non compliant and deviated from their OA Tp 0% of Path, Header and Form were non compliant and deviated from their OAS 01
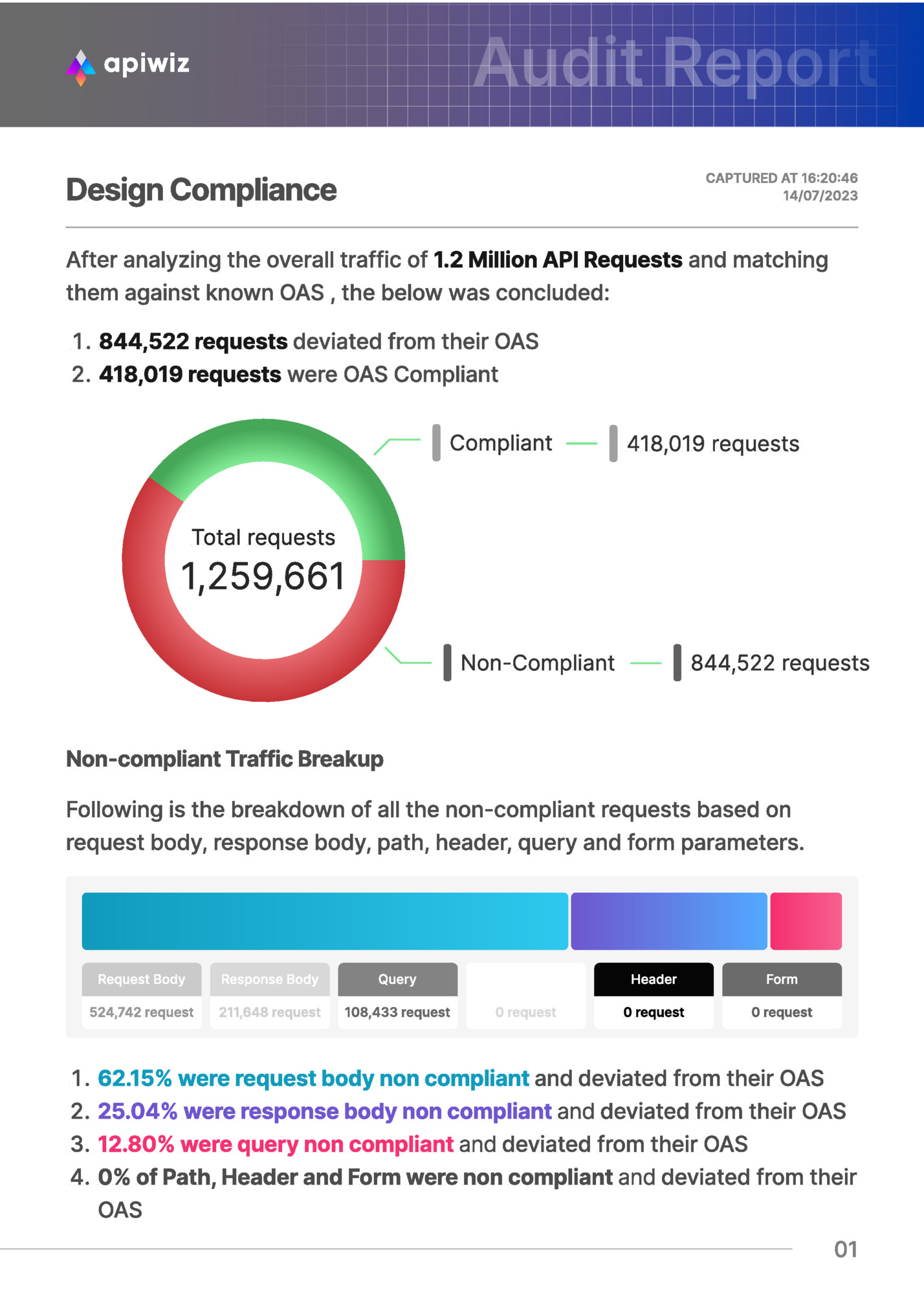
CAPTURED AT 16:20:46 14/07/2023 After analyzing the overall traffic of 1.2 Million API Requests and matching them against known OWASP Top 10 security patterns, the below was concluded: Secured 1,125,182 requests Total Traffic 1,382,192 Un-secured 241,644 requests Security Threat Breakup Here is the breakdown of all the vulnerable requests matched against known OWAS Top 10 API security threat patterns including SQL, XPATH, Javascript, and server side. SQL Javascript Server side 165,273 requests ² ² ² ² XPATH 69,800 requests 6,300 requests 173 requests 68.30% of requests matched against known SQL threat patterns 28.86% of requests matched against known XPATH threat patterns 2.90% of requests matched against known Javascript threat patterns 0.07% of requests matched against known server side threat patterns 02
SQL: SQL injection is a code injection technique that allows an attacker to manipulate or execute unauthorized SQL commands through input fields on a website, potentially leading to data breaches or unauthorized access to a database. XPATH: XPath attacks are a type of injection attack that exploit vulnerabilities in applications that use XPath to query XML data, allowing attackers to bypass security measures, extract sensitive information, or modify the behavior of the application. Javascript: Injection of malicious JavaScript code into an API payload, which when executed by the client's browser, can lead to various security risks such as cross-site scripting (XSS) attacks or unauthorized access to sensitive user data. Server side: The execution of reserved or privileged system functions through command injection can lead to unauthorized access, manipulation and or deletion of mission critical data. 03

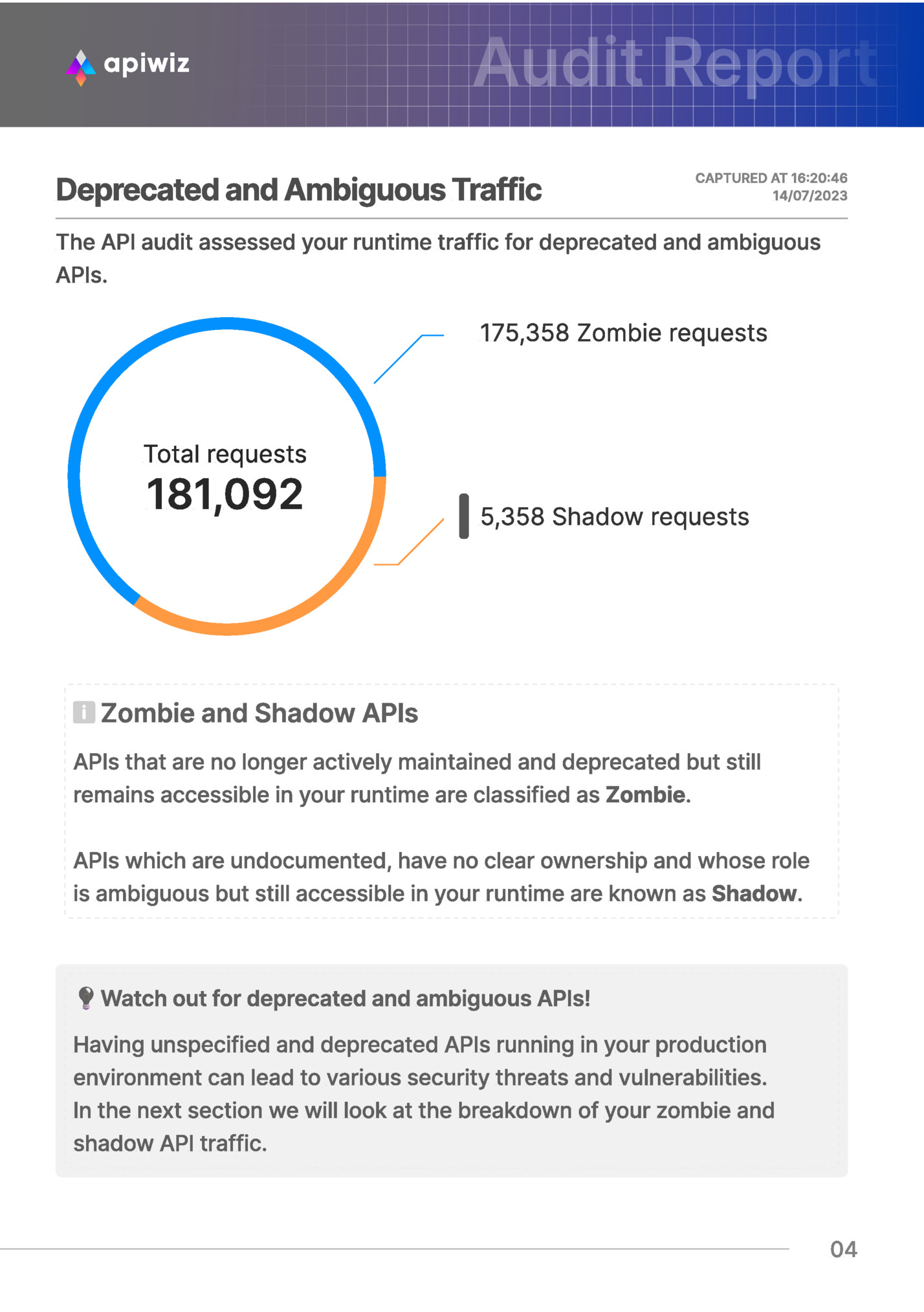
CAPTURED AT 16:20:46 14/07/2023 The API audit assessed your runtime traffic for deprecated and ambiguous APIs. 175,358 Zombie requests Total requests 181,092 5,358 Shadow requests Zombie and Shadow APIs APIs that are no longer actively maintained and deprecated but still remains accessible in your runtime are classified as Zombie. APIs which are undocumented, have no clear ownership and whose role is ambiguous but still accessible in your runtime are known as Shadow. Watch out for deprecated and ambiguous APIs! Having unspecified and deprecated APIs running in your production environment can lead to various security threats and vulnerabilities. In the next section we will look at the breakdown of your zombie and shadow API traffic. 04
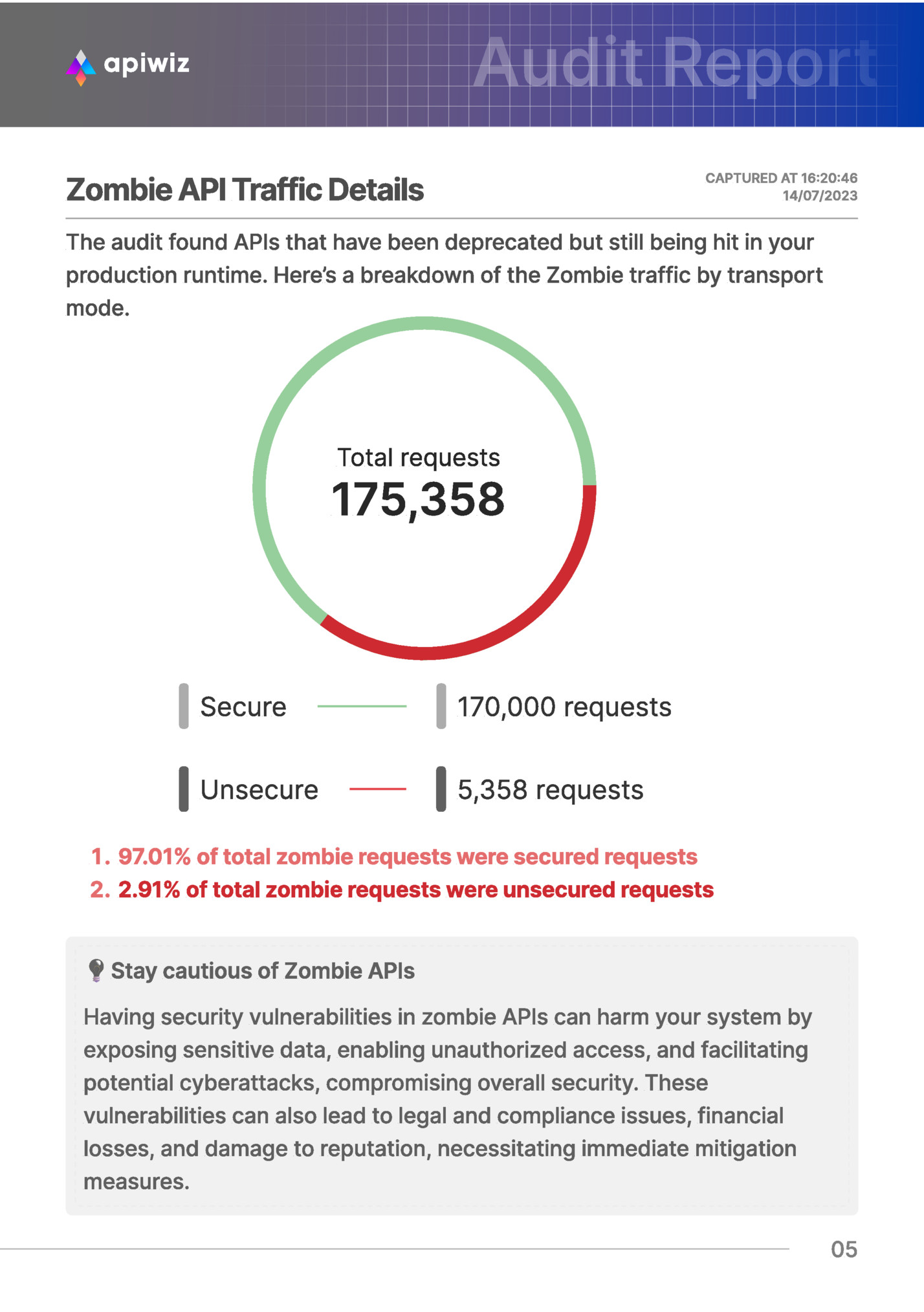
CAPTURED AT 16:20:46 14/07/2023 The audit found APIs that have been deprecated but still being hit in your production runtime. Here’s a breakdown of the Zombie traffic by transport mode. Total requests 175,358 Secure 170,000 requests Unsecure 5,358 requests 97.01% of total zombie requests were secured request 2.91% of total zombie requests were unsecured requests Stay cautious of Zombie APIs Having security vulnerabilities in zombie APIs can harm your system by exposing sensitive data, enabling unauthorized access, and facilitating potential cyberattacks, compromising overall security. These vulnerabilities can also lead to legal and compliance issues, financial losses, and damage to reputation, necessitating immediate mitigation measures. 05
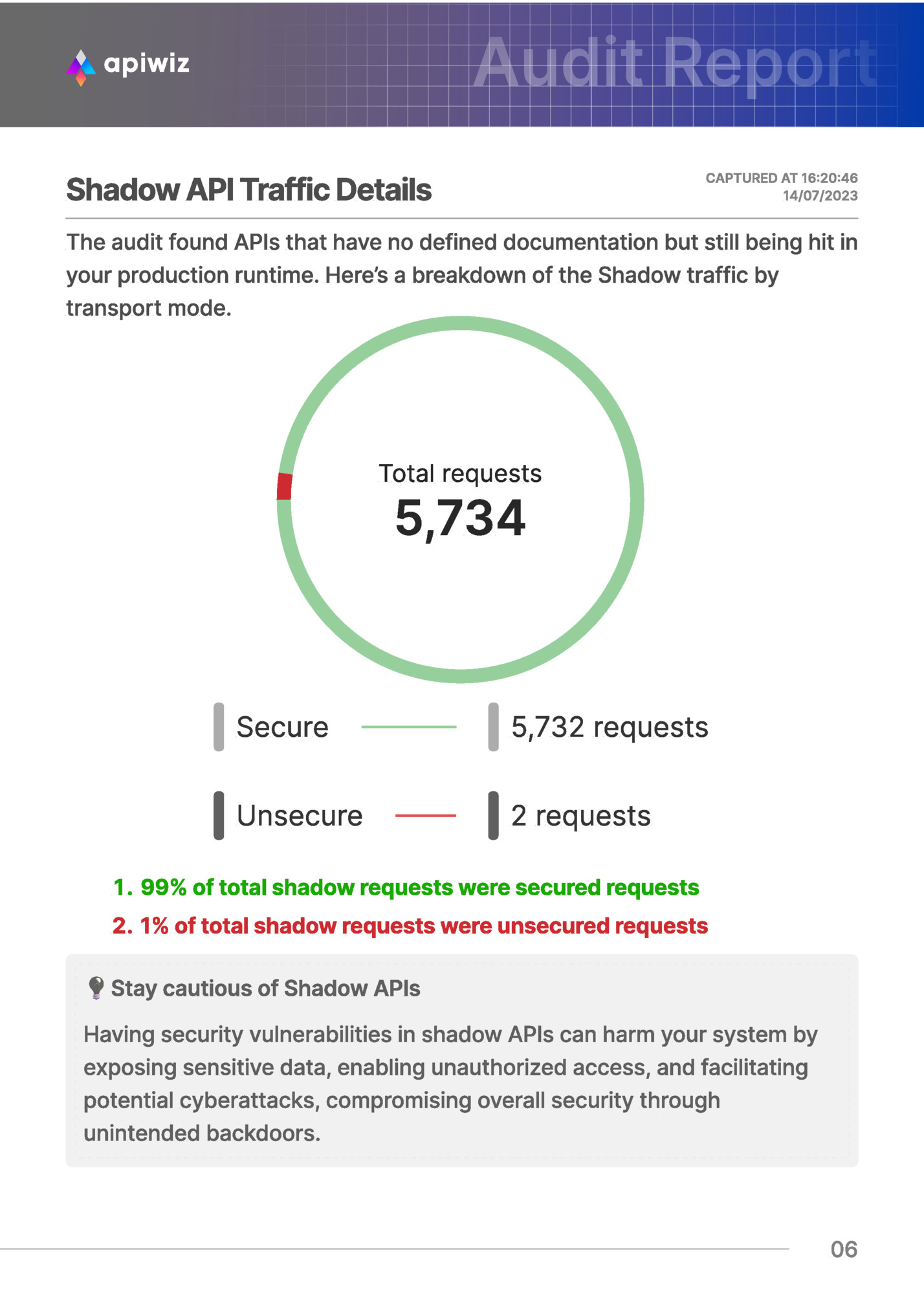
CAPTURED AT 16:20:46 14/07/2023 The audit found APIs that have no defined documentation but still being hit in your production runtime. Here’s a breakdown of the Shadow traffic by transport mode. Total requests 5,734 Secure 5,732 requests Unsecure 2 requests }w 99% of total shadow requests were secured requests w 1% of total shadow requests were unsecured requests Stay cautious of Shadow APIs Having security vulnerabilities in shadow APIs can harm your system by exposing sensitive data, enabling unauthorized access, and facilitating potential cyberattacks, compromising overall security through unintended backdoors. 06
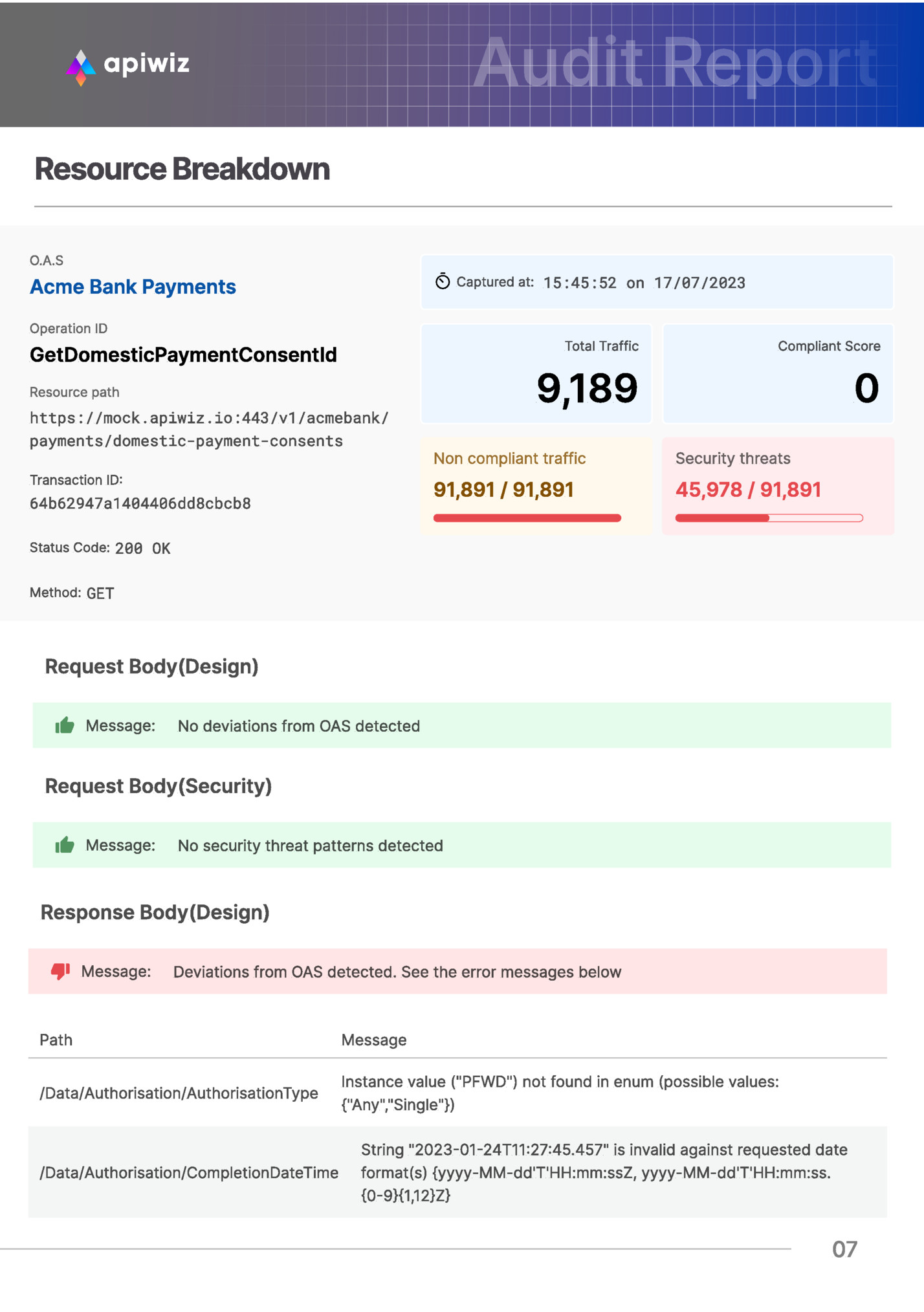
Acme Bank Payments GetDomesticPaymentConsentId 9,189 91,891 / 91,891 0 45,978 / 91,891 07
Fleepit Digital © 2021