VOL.1 S T U D I O S INFORMATION SECURITY BTECH 3RD YEAR UNIT 1 TO UNIT 5 35 PAGES

Information Security/Unit-1 INFORMATION SECURITY UNIT – 1 I ntroduction to Information Security SECURITY ATTACK Any action that Comprises the Security of information owned by an organization. IS all about how to prevent attacks. or failing that to detect attack on information based system, there аrе two type of attack → Active Attack Are the type of attack in which, the attacker efforts to change or modify the content of message The most important thing in Active Attack is that, the Victim gets informed about the attack It is dangerous do Integrity. as well as availability. → Passive Attack P assive Attack are the type of Attack in which attacker observe the Content of message or Copies the Content of message It is dangerous to Confidentiality There is no harm in the System To Passive Attacks, Victim does not get informed about the attack INTERRUPTION A n asset of the system is destroyed or become unavailable. It is an attack of availability Ex – destruction of some hardware , jamming wireless networks 1

Information Security/Unit-1 Interception An unauthorized Party gains access to assets . It is an attack of confidentiality Ex ;- Copying dado ar program) Eavesdropping Modification An unauthorized party gains. Access to assets. and tampers on Assets . Attacks are on integrity . Ex ; Changing Data File , Altering message a program & the Content. Fabrication An Fabrication attacks creates illegitimate processes or other data within a system Ex-- Hackers gaining access to personal email, sending message SECURITY SERVICES [End Sem 2018 -2M] A processing or communication service that enhances the Security of the data processing system & the information transfer of an organization. TYPES ; 1 AUTHENTICATION 2 CONFIDENTIALITY 3 INTEGRITY 4 ACCESS CONTROL 5 NON REPUDIATION 1 AUTHENTICATION • This Verifies the identity of an user or entity trying to access data or System. It Ensures only authorized users get access to data. 2. CONFIDENTIALITY It aims to prevent Unauthorized access To Sensitive data. It ensures that information remains private .Encryption is a primary technique to reach confidentiality 3 INTEGRITY 2

Information Security/Unit-1 It ensures that data remain accurate , and trustworthy. Safeguard data against unauthorized modification or tampering of data . Hash function and digital signature are used in it . types are :Connection oriented integrity service :- it deals with the stream of message means message received or sent with no duplication. Connectionless oriented integrity service :- it deals with the individual message regardless of less context . 4 NON REPUDIATION It ensures that users cannot deny their actions or transactions . It provide proof of the origin and integrity of data 5 ACCESS CONTROL It enforces rules and regulations for resource access . It restricts unauthorized users . SECURITY MECHANISM 1 DIGITAL SIGNATURE ;- IT VERIFIES THE AUTHENTICATION AND INTEGRITY A DIGITAL DOCUMENT . 2 ACCESS CONTROL 3 DIGITAL SIGNATURE 4 TRAFFIC PADDING :_ INSERTION OF BITS INTO GAPS IN DATA STREAM TO FRUSTRATE TRAFFIC ANALYSIS ATTEMPT CLASSICAL ENCRYPTION TECHNIQUE : CIPHER TEXT ; THE CODED MESSAGE CIPHER ;- Algo for transforming plain – cipher text KEY : info used in cipher known only to sender and receiver CRYPTOGRAPHY ; Study of encryption principle methods. CRYPTOLOGY : the field of both cryptography and cryptanalysis. CRYPTOGRAPHY Cryptography is the process of hiding or coding information so that only the person a message was intended for can read it. There are two processes in it , encryption and decryption performed at sender and receiver's state respectively . TYPES :- CLASSICAL AND QUANTUM 3

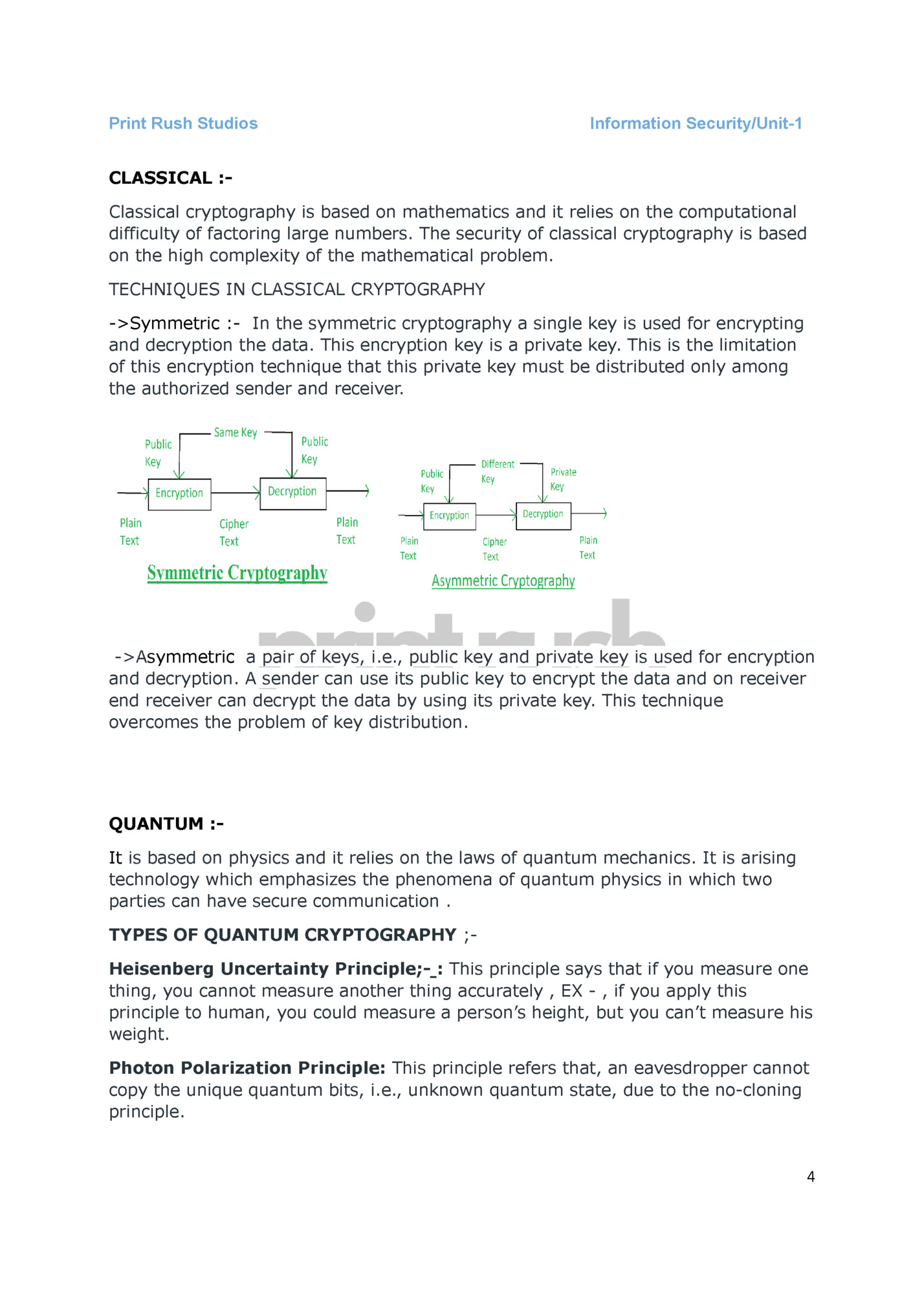
Information Security/Unit-1 CLASSICAL :Classical cryptography is based on mathematics and it relies on the computational difficulty of factoring large numbers. The security of classical cryptography is based on the high complexity of the mathematical problem. TECHNIQUES IN CLASSICAL CRYPTOGRAPHY ->Symmetric :- In the symmetric cryptography a single key is used for encrypting and decryption the data. This encryption key is a private key. This is the limitation of this encryption technique that this private key must be distributed only among the authorized sender and receiver. ->Asymmetric a pair of keys, i.e., public key and private key is used for encryption and decryption. A sender can use its public key to encrypt the data and on receiver end receiver can decrypt the data by using its private key. This technique overcomes the problem of key distribution. QUANTUM :It is based on physics and it relies on the laws of quantum mechanics. It is arising technology which emphasizes the phenomena of quantum physics in which two parties can have secure communication . TYPES OF QUANTUM CRYPTOGRAPHY ;Heisenberg Uncertainty Principle;- : This principle says that if you measure one thing, you cannot measure another thing accurately , EX - , if you apply this principle to human, you could measure a person’s height, but you can’t measure his weight. Photon Polarization Principle: This principle refers that, an eavesdropper cannot copy the unique quantum bits, i.e., unknown quantum state, due to the no-cloning principle. 4
Information Security/Unit-1 TECHNIQUES :SUBSTITUTION TECHNIQUES :- The substitution technique involves replacing letters with other letters and symbols. In simple terms, the plaintext characters are substituted, and additional substitute letters, numerals, and symbols are implemented in their place. TYPES : - CAESAR CIPHER [End Sem 2019-3M] It is a type of substitution cipher in which each letter in the plaintext is replaced by a letter some fixed number of positions down the alphabet. PLAYFAIR CIPHER [Most Imp] It encrypts pair of letter at a time using 5* 5 matrix . It adds variability , make it difficult to decrypt . rules ;Diagram 1 repeating letter – filler letter 2 same column - | ↓.| wrap around 3 same row - | →|wrap around 4 rectangle :- |→← |swap around Plain text :- attack Diagram :- at Play fair RS ta mosque ck SR mo sq ue DE (BY RULES ) ON TS ML 5

Information Security/Unit-1 MONOALPHABETIC CIPHER :A monoalphabetic cipher is a type of substitution cipher where each letter of the plaintext is replaced with another letter of the alphabet. POLYALPHABETIC CIPHER :A polyalphabetic cipher is a substitution cipher that uses multiple substitution alphabets EX ;- if A is replaced by B in the first letter of a message, it might be replaced by R if it's the second letter, and E if it's the third letter. TRANSPORTATION TECHNIQUES : A transposition cipher is a type of encryption that rearranges the order of characters in a plaintext message to create a ciphertext message instead of replacing . TYPES : Rail Fence :- Writes plain text as a sequence of diagonals and then reads it row by row to produce the ciphertext. Plain Text: meet me Tomorrow Row Transposition Technique : - a more complex transposition write letters of message out in rows over a specified number of columns (key length)Then reorder the columns according to some key before re adding off the rows. 6

STENOGRAPHY Information Security/Unit-1 [End Sem 2019-5M] Steganography is the technique of hiding data within an ordinary, nonsecret file or message to avoid detection; the hidden data is then extracted at its destination. Steganography use can be combined with encryption as an extra step for hiding or protecting data. Steganography can be used to conceal almost any type of digital content, including text, image, video or audio content. The secret data can be hidden inside almost any other type of digital content. There are various type of stenography some are Image Steganography: ● Conceals information within images. ● Alters pixel values or embeds data in the least significant bits. ● Examples include hiding text within an image or embedding a file in an image file. Text Steganography: ● Embeds messages within seemingly innocuous text. ● Modifies spacing, font styles, or other text properties to hide information. ● Often used in social media posts or emails. Audio Steganography: ● Hides data within audio files. ● Alters frequencies or embeds information in silent parts of audio. ● Used for covert communication or watermarking. Steganography Examples Include :● Writing with invisible ink ● Embedding text in a picture (like an artist hiding their initials in a painting they’ve done) ● Backward masking a message in an audio file (remember those stories of evil messages recorded backward on rock and roll records?) ● Concealing information in either metadata or within a file header 7

Information Security/Unit-1 To Access The Complete Printed Module, Delivered To The Comfort Of Your Homes Visit The Link -https://www.printrushstudios.online/purchase-modules https://wa.me/message/6TYFOEZULHEOI1 Or Whatsapp Us at - +91 92445 78723 For Single Module Any 1 Subject All Units Covered - ₹99 For Bundle Of All Subjects Covered Including Electives - ₹299 Orders Dispatching From Monday Onwards. 8

Fleepit Digital © 2021