VOL.1 S T U D I O S COMPUTER NETWORKING BTECH 3RD YEAR UNIT 1 TO UNIT 5 35 PAGES

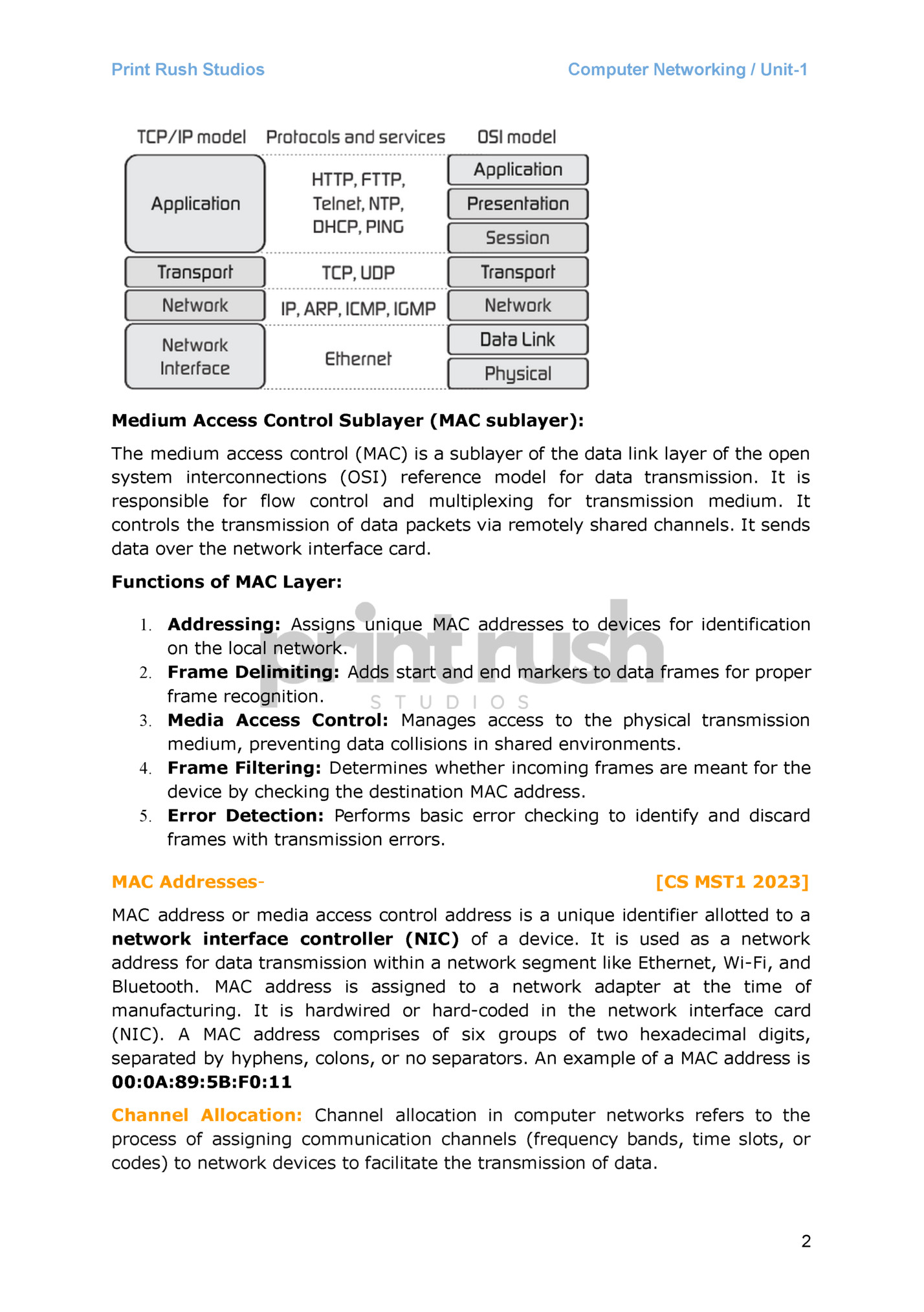
Computer Networking / Unit-1 Unit – 1 OSI model: The Open Systems Interconnection (OSI) model describes seven layers that computer systems use to communicate over a network. It was the first standard model for network communications TCP-IP Model: The TCP/IP model is a four-layer model that divides network communications into four distinct categories or layers: 1

Computer Networking / Unit-1 Medium Access Control Sublayer (MAC sublayer): The medium access control (MAC) is a sublayer of the data link layer of the open system interconnections (OSI) reference model for data transmission. It is responsible for flow control and multiplexing for transmission medium. It controls the transmission of data packets via remotely shared channels. It sends data over the network interface card. Functions of MAC Layer: 1. Addressing: Assigns unique MAC addresses to devices for identification on the local network. 2. Frame Delimiting: Adds start and end markers to data frames for proper frame recognition. 3. Media Access Control: Manages access to the physical transmission medium, preventing data collisions in shared environments. 4. Frame Filtering: Determines whether incoming frames are meant for the device by checking the destination MAC address. 5. Error Detection: Performs basic error checking to identify and discard frames with transmission errors. MAC Addresses- [CS MST1 2023] MAC address or media access control address is a unique identifier allotted to a network interface controller (NIC) of a device. It is used as a network address for data transmission within a network segment like Ethernet, Wi-Fi, and Bluetooth. MAC address is assigned to a network adapter at the time of manufacturing. It is hardwired or hard-coded in the network interface card (NIC). A MAC address comprises of six groups of two hexadecimal digits, separated by hyphens, colons, or no separators. An example of a MAC address is 00:0A:89:5B:F0:11 Channel Allocation: Channel allocation in computer networks refers to the process of assigning communication channels (frequency bands, time slots, or codes) to network devices to facilitate the transmission of data. 2
Types of Channel Allocation: Computer Networking / Unit-1 [CS MST1 2023] 1. Static Channel Allocation: ● In static channel allocation scheme, a fixed portion of the frequency channel is allotted to each user. For N competing users, the bandwidth is divided into N channels using frequency division multiplexing (FDM), and each portion is assigned to one user. This scheme is also referred as fixed channel allocation or fixed channel assignment. ● In this allocation scheme, there is no interference between the users since each user is assigned a fixed channel. However, it is not suitable in case of a large number of users with variable bandwidth requirements. 2. Dynamic Channel Allocation: ● ● In dynamic channel allocation scheme, frequency bands are not permanently assigned to the users. Instead channels are allotted to users dynamically as needed, from a central pool. The allocation is done considering a number of parameters so that transmission interference is minimized. This allocation scheme optimises bandwidth usage and results is faster transmissions. MAC Protocols: 1. Random Access Protocols: In this protocol, all the station has the equal priority to send the data over a channel. In random access protocol, one or more stations cannot depend on another station nor any station control another station. Depending on the channel's state (idle or busy), each station transmits the data frame. Types of Random Access Protocols: a. ALOHA: It is designed for wireless LAN (Local Area Network) but can also be used in a shared medium to transmit data. Using this method, any station can transmit data across a network simultaneously when a data frameset is available for transmission. ALOHA Rules 1. Any station can transmit data to a channel at any time. 2. It does not require any carrier sensing.Collision and data frames may be lost during the transmission of data through multiple stations. 3. Acknowledgment of the frames exists in Aloha. Hence, there is no collision detection. It requires retransmission of data after some random amount of time. Types of ALOHA: 3

1. Pure ALOHA- Computer Networking / Unit-1 [BTECH END SEM 2019,IT 2019] Whenever data is available for sending over a channel at stations, we use Pure Aloha. In pure Aloha, when each station transmits data to a channel without checking whether the channel is idle or not, the chances of collision may occur, and the data frame can be lost. When any station transmits the data frame to a channel, the pure Aloha waits for the receiver's acknowledgment. If it does not acknowledge the receiver end within the specified time, the station waits for a random amount of time, called the backoff time (Tb). And the station may assume the frame has been lost or destroyed. Therefore, it retransmits the frame until all the data are successfully transmitted to the receiver. 1. The total vulnerable time of pure Aloha is 2 * Tfr. 2. Maximum throughput occurs when G = 1/ 2 that is 18.4%. 3. Successful transmission of data frame is S = G * e ^ - 2 G. 4. The maximum efficiency of Pure Aloha is very less due to large number of collisions. 2. Slotted ALOHA- The slotted Aloha is designed to overcome the pure Aloha's efficiency because pure Aloha has a very high possibility of frame hitting. In 4
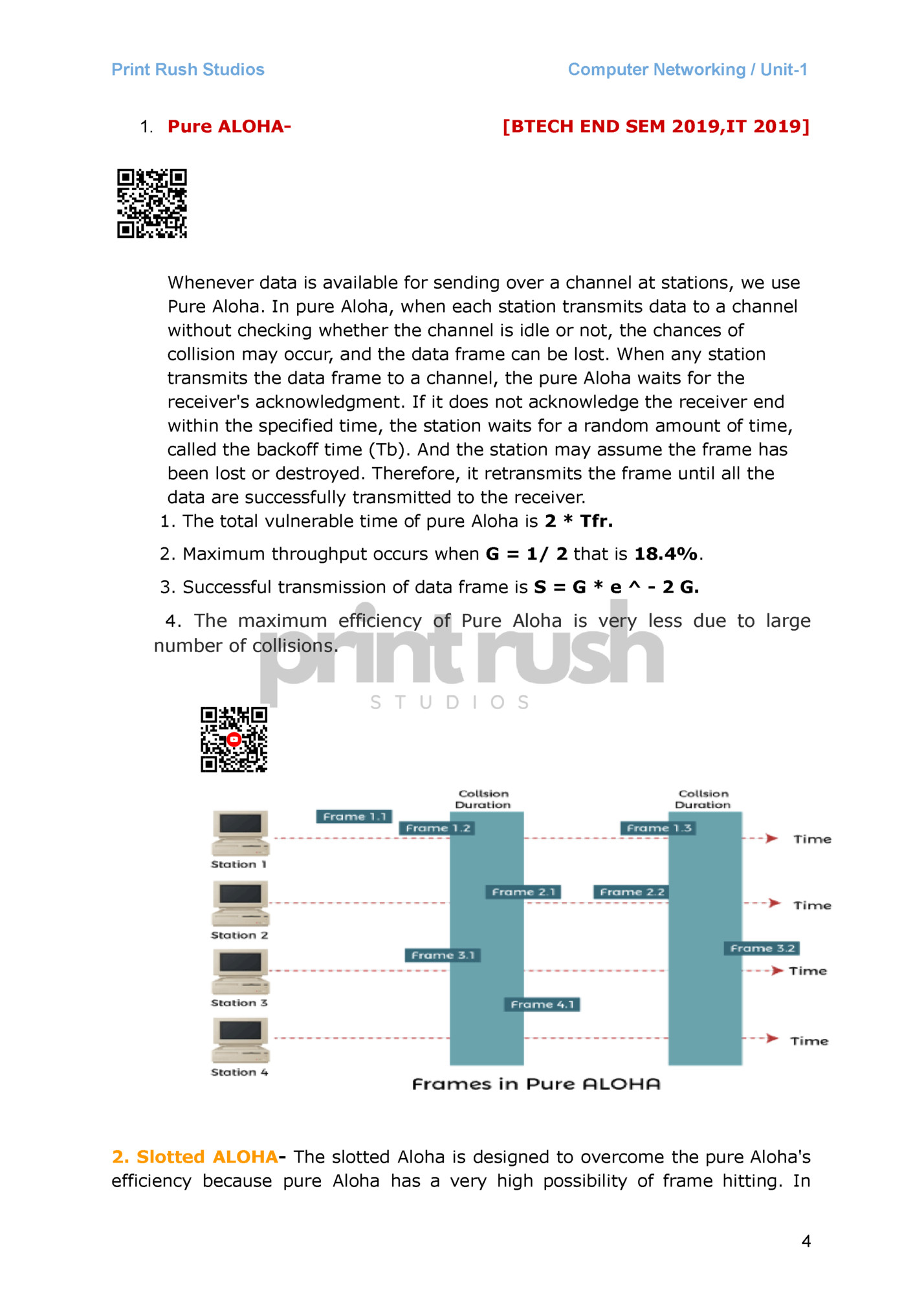
Computer Networking / Unit-1 slotted Aloha, the shared channel is divided into a fixed time interval called slots. So that, if a station wants to send a frame to a shared channel, the frame can only be sent at the beginning of the slot, and only one frame is allowed to be sent to each slot. And if the stations are unable to send data to the beginning of the slot, the station will have to wait until the beginning of the slot for the next time. However, the possibility of a collision remains when trying to send a frame at the beginning of two or more station time slot. 1. Maximum throughput occurs in the slotted Aloha when G = 1 that is 37%. 2. The probability of successfully transmitting the data frame in the slotted Aloha is S = G * e ^ - 2 G. 3. The maximum efficiency of Slotted Aloha is high due to less number of collisions. Difference Between Pure Aloha And Slotted Aloha- [END SEM 2019] Pure Aloha Slotted Aloha Any station can transmit the data at any time. Any station can transmit the data at the beginning of any time slot. The time is continuous and not globally synchronized. The time is discrete and globally synchronized. Vulnerable time in which collision may occur = 2 x Tt Vulnerable time in which collision may occur = Tt Probability of successful transmission of data packet = G x e-2G Probability of successful transmission of data packet = G x e-G Maximum efficiency = 18.4% (Occurs at G = 1/2) Maximum efficiency = 36.8% ( Occurs at G = 1) The main advantage of pure aloha is its simplicity in implementation. The main advantage of slotted aloha is that it reduces the number of collisions to half and doubles the efficiency of pure aloha. 5

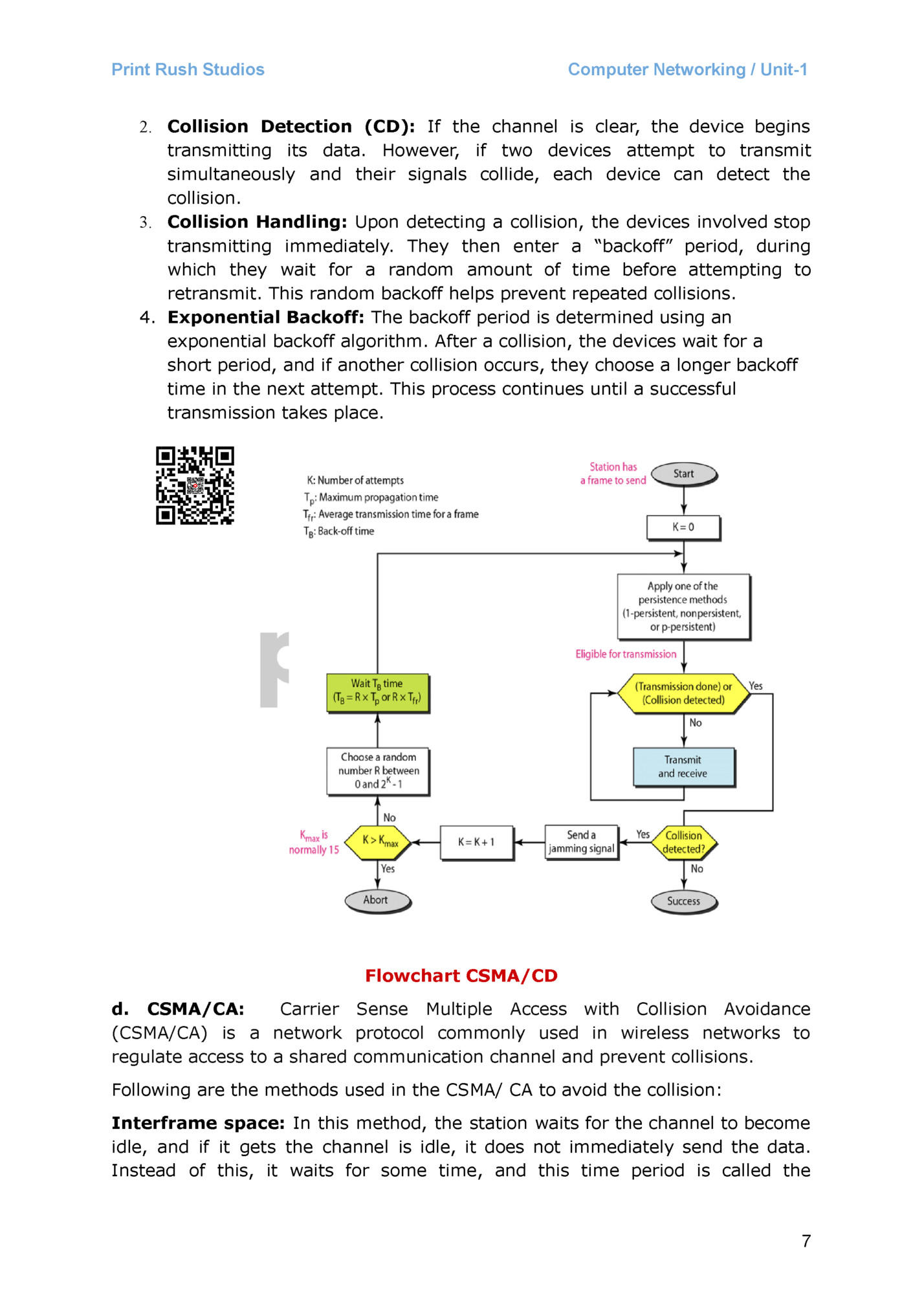
Computer Networking / Unit-1 b. CSMA(Carrier Sense Multiple Access): It is used to sense the traffic on a channel (idle or busy) before transmitting the data. It means that if the channel is idle, the station can send data to the channel. Otherwise, it must wait until the channel becomes idle. Hence, it reduces the chances of a collision on a transmission medium. 1-Persistent CSMA: In 1-persistent CSMA, if a node senses the channel as idle, it transmits immediately. If the channel is busy, the node waits until it becomes idle. Non-Persistent CSMA: In non-persistent CSMA, if a node senses the channel as busy, it defers its transmission for a random period before checking the channel again. P-Persistent: It is the combination of 1-Persistent and Non-persistent modes. The P-Persistent mode defines that each node senses the channel, and if the channel is inactive, it sends a frame with a P probability. If the data is not transmitted, it waits for a (q = 1-p probability) random time and resumes the frame with the next time slot. O- Persistent: It is an O-persistent method that defines the superiority of the station before the transmission of the frame on the shared channel. If it is found that the channel is inactive, each station waits for its turn to retransmit the data. C. CSMA/CD: [END SEM 2019] Carrier Sense Multiple Access with Collision Detection (CSMA/CD) is a network protocol used in Ethernet networks to manage access to a shared communication channel. CSMA/CD helps to detect and manage collisions when they happen. 1. Carrier Sense (CS): Before transmitting data, a device using CSMA/CD listens to the network to determine if the channel is busy (i.e., whether another device is currently transmitting). 6

Computer Networking / Unit-1 2. Collision Detection (CD): If the channel is clear, the device begins transmitting its data. However, if two devices attempt to transmit simultaneously and their signals collide, each device can detect the collision. 3. Collision Handling: Upon detecting a collision, the devices involved stop transmitting immediately. They then enter a “backoff” period, during which they wait for a random amount of time before attempting to retransmit. This random backoff helps prevent repeated collisions. 4. Exponential Backoff: The backoff period is determined using an exponential backoff algorithm. After a collision, the devices wait for a short period, and if another collision occurs, they choose a longer backoff time in the next attempt. This process continues until a successful transmission takes place. Flowchart CSMA/CD d. CSMA/CA: Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA) is a network protocol commonly used in wireless networks to regulate access to a shared communication channel and prevent collisions. Following are the methods used in the CSMA/ CA to avoid the collision: Interframe space: In this method, the station waits for the channel to become idle, and if it gets the channel is idle, it does not immediately send the data. Instead of this, it waits for some time, and this time period is called the 7
Computer Networking / Unit-1 Interframe space or IFS. However, the IFS time is often used to define the priority of the station. Contention window: In the Contention window, the total time is divided into different slots. When the station/ sender is ready to transmit the data frame, it chooses a random slot number of slots as wait time. If the channel is still busy, it does not restart the entire process, except that it restarts the timer only to send data packets when the channel is inactive. Acknowledgment: In the acknowledgment method, the sender station sends the data frame to the shared channel if the acknowledgment is not received ahead of time. Flowcart CSMA/CA Collision Free Protocols 8

Fleepit Digital © 2021